Windows Analytics is the suite name following the original release of Upgrade readiness. The suite adds Device Health and Update Compliance under the same roof. Depending on the environment each sub-product will provide key information for end-user computer admins. Windows Analytics and Log Analytics is better together!
Upgrade readiness can help assess applications and drivers compatibility prior to migrate from Windows 7/8.1 to Windows 10, or even from one Windows 10 build to another.
Device Health provides extra information for admins to review various crash within their environment.
Update compliance provides a way to track how updates and upgrades are doing in the environment. This will be particularly useful when mixed with Windows Update for Business.
All of the Windows Analytics features sit on Log Analytic from Azure. Previously it was possible to host the data in OMS. OMS as retired and it is possible to move it into Log Analytics.
In this post, we will show how to configure Windows Analytics with Log Analytics
Windows Analytics Log Analytics Requirements
- Rights to create the Log Analytics :
- Global admin
- Contributor on the associated Azure subscription
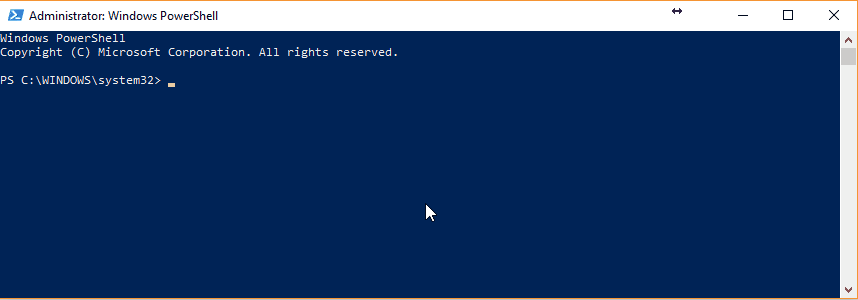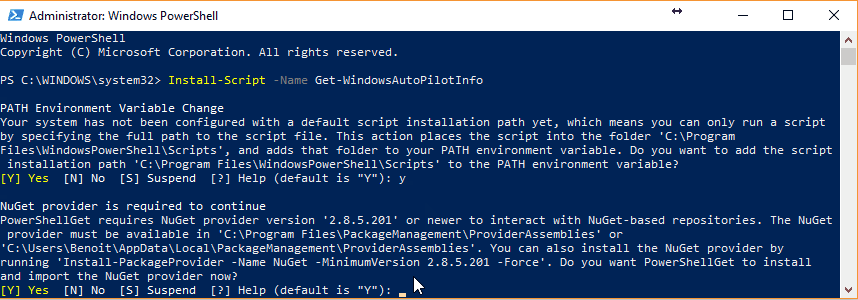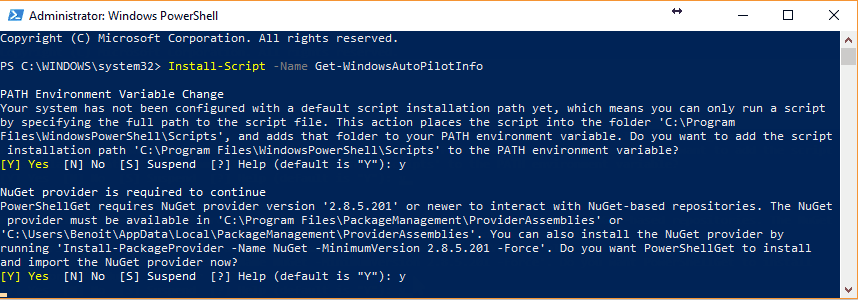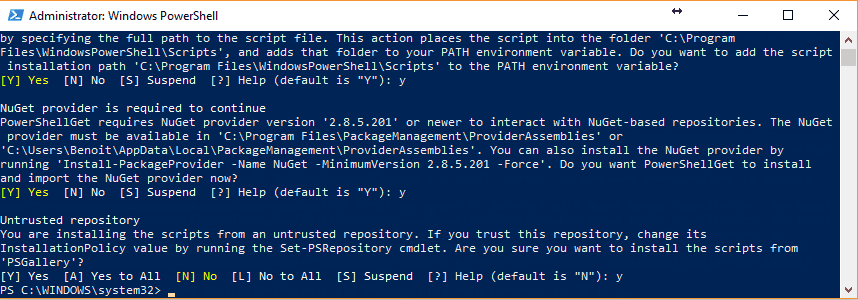
- Download the Upgrade readiness deployment script here
- For Upgrade readiness clients
- Windows 7 or higher
- For Update compliance clients
- Windows 10 Pro or higher
- Semi-annual channel or LTSC
- For DEvice health clients
- Windows 10 Enterprise or Education
Configure Log Analytics workspace
- Go to Azure portal
- Click on Create a resource and search for Log Analytics. Once found, click Create

- Select Create New
- Select the Subscription type.
- The resource group can be a new or existing one.
- The pricing tier will be Per GB

Pricing Tier
Previously with OMS, it was clear that Windows Analytics was free. Moving to Log Analytics, it is still a free service. But when selecting the Pricing tier, the Free option is no longer available. Seems that if you still see the Free tier, it’s likely because OMS with Upgrade readiness was configured before.
For newer environment, the option of Per GB will be the only choice. but again, it remains free. Looking at the data usage in Log Analytics, we can see that the content is not billable.

- Click Ok to create the Log Analytics. this will take a little time to complete.

Configure Upgrade Readiness
- Go to Azure portal
- Click on Create a resource and search for Upgrade Readiness

- Click Create

- Click on Select a Workspace under the Log Analytics Workspace, and then select the one created in the previous step

- Click Create at the bottom
Configure Device Health
- Go to Azure portal
- Click on Create a resource and search for Device Health. Click Create

- Click on Select a Workspace under the Log Analytics Workspace, and then select the one created in the previous step

- Click Create at the bottom
Configure Update Compliance
- Go to Azure portal
- Click on Create a resource and search for Device Health. Click Create

- Click on Select a Workspace under the Log Analytics Workspace, and then select the one created in the previous step

- Click Create at the bottom
Access Windows Analytics components
- Go to Azure portal
- Search for Log Analytics and select Log Analytics Workspaces

- Click on the Log Analytics for the 3 Windows Analytics components

- Select Solutions. The 3 Windows Analytics components are available.

- To make it easy to access, pin each summary to the Azure Dashboard. Click on any one of the 3 and select Pin to dashboard from the Summary.

Configure data collection for Windows Analytics with the script
The computers that you want to evaluate needs to run a script to send their data.
To do so :
- Download the Upgrade Readiness deployment script
- Extract the zip file
- Edit .\ UpgradeAnalytics092816\Deployment\RunConfig.bat file
- Change the following values :
- LogPath : Where you want the logs to be saved
- CommercialIDValue : Enter your commercial key
- Logmode : 1
- Deploy the script using any methods
- Once deployed, it will take a good 2 to 3 days before data starts populating in the 3 components of Windows Analytics. This will be the same no matter which solution is chosen to enable Windows Analytics on clients.
Commercial ID
To find the CommercialID:
- Go to Upgrade readiness and select Solution settings

- Under Upgrade Readiness settings, the CommercialID is available.

Configure data collection for Windows Analytics with Intune
Most settings for Windows Analytics are configured by OME-URI items.
- In a device restriction profile, under Reporting and Telemetry make the Share user Data up to Enhanced

This will only configure the level of usage data. It will not prevent user modification.
Diagnostic data
Depending on the features used with Windows Analytics, setting the diagnostic data below Enhanced will limit capabilities like Device Health.
Microsoft recommends Enhanced for Windows 10 1709 or higher for full functionality from Windows Analytics.
For more details about Diagnostic data, see Microsoft Docs.
- Create a new Device configuration profile

- Specify the name, select Windows 10 and later and select a Custom profile type

- There are multiple OMA-URI settings available for Window Analytics. The first and mandatory OMA-URI is the CommercialID
- Name : CommercialID
- OME-URI : ./Vendor/MSFT/DMClient/Provider/MS DM Server/CommercialID
- Value, type string: <yourCommercialID>

- To disable the ability for the user to change the usage data level, set the following OMA-URI
- Name : ConfigureTelemetryOptInSettingsUx
- OME-URI : ./Vendor/MSFT/Policy/Config/System/ConfigureTelemetryOptInSettingsUx
- Value, type integer : 1

- To prevent user notification when modifying the usage data level, set the following OMA-URI
- Name : ConfigureTelemetryOptInChangeNotification
- OMA-URI : ./Vendor/MSFT/Policy/Config/System/ConfigureTelemetryOptInChangeNotification
- Value type integer : 1

- Other possible configurations are related to GDPR for EU company.
- Name : LimitEnhancedDiagnosticDataWindowsAnalytics
- OMA-URI: ./Vendor/MSFT/Policy/Config/System/LimitEnhancedDiagnosticDataWindowsAnalytics
- Value type integer : 1
- And..
- Name : AllowDeviceNameInDiagnosticData
- OMA-URI: ./Vendor/MSFT/Policy/Config/System/AllowDeviceNameInDiagnosticData
- Value type integer: 1
- Be aware that this setting, if disabled, will provide limited data analysis from Update compliance and device health because of the computer name not available.
Configure data collection for Windows Analytics with GPO
As covered in the Intune section, the same settings are available in the GPO. They can be found under Computer Configuration/Administration Templates/Windows Components/Data Collection and Preview build.
Make sure to use the latest ADMX for the most up to date options.

For more details about the various settings, see Microsoft Docs
Enable client for Windows Analytics with SCCM
If you are using SCCM, the Commercial ID can be specified in the Client settings. This is by far the easiest method of all. Otherwise, this option is limited as more configuration is available by GPO and Intune

For more details about Windows analytics, see Microsoft docs
[ratings]Share this Post
Contributor of System Center Dudes. Based in Montreal, Canada, Senior Microsoft SCCM consultant, working in the industry for more than 10 years. He developed a strong knowledge of SCCM and MDT to build automated OS deployment solution for clients, managed large and complexe environment, including Point of Sale (POS) related projects.
The post How to configure Windows Analytics with Log Analytics appeared first on System Center Dudes.